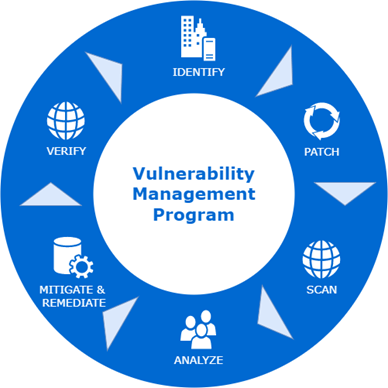
Vulnerability management process diagram: simplifying your security Flowchart for vulnerability assessment. Answered: using the vulnerability assessment process flow di
Vulnerability Management Process Flow Chart | Rootshell
The vulnerability management process after equifax
Vulnerability strategy
What is vmdr (vulnerability management, detection and response)?Vulnerability management process, what is it? – conviso appsec Vulnerabilities are beyond what you thinkVulnerability management program: quick start guide.
4 steps of vulnerability remediation processVulnerability management services Vulnerability management servicesVulnerability management.

Vulnerability manageengine gain thorough
Vulnerability management patch process network metrics program importance medium gif systems marchVulnerability remediation vulnerabilities snyk Top 7 vulnerability management process flow chart templates withVulnerability management process diagram photo by mysticboard.
Vulnerability process sequence logicVulnerability management The five stages of vulnerability managementThe vulnerability management lifecycle (5 steps).

What is vulnerability management?
Creating a vulnerability management strategyVulnerability management process flow equifax after What is vulnerability management? how does it workVulnerability and patch management process flow ppt slide.
Vulnerability workflow vulnerabilities identifyVulnerability management process ppt powerpoint presentation Vulnerability assessment best practicesVulnerability gartner.
Vulnerability assessment process
Vulnerability management templateVulnerability flowchart assessment Vulnerability process management template creately diagram flowchartVulnerability management process flow powerpoint ppt template bundles.
Vulnerability process diagram management photobucketVulnerability management cycle crowdstrike Vulnerability management process, what is it? – conviso appsecVulnerability management lifecycle.

Vulnerability management process flow chart
Vulnerability aimed prioritizing protecting analyzingVulnerability practices identification attackers approval pdfs Vulnerability lifecycle crowdstrike reassess actMust have metrics for vulnerability management.
Vulnerability management process — openstack security advisories 0.0.1What is vulnerability management? : definition & process What is vulnerability management? why does it matter?Vulnerability detect.

Process security vulnerability management openstack vmt fixing steps reception sig report advisories ossa
.
.